Symantec 2014 Annual Report Download - page 3
Download and view the complete annual report
Please find page 3 of the 2014 Symantec annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
Dear Fellow Shareholders:
The world has continued to see a marked increase in the number of major
data breaches and cyber attacks, including high-profile penetrations at major
retailers and state-sponsored attacks on media and government websites.
Enterprises, governments, and individuals need help now more than ever navigating
the complex, rapidly evolving cyber security landscape. No company is better
positioned to address these challenges than Symantec.
While most know us for our leading Norton security offerings, one of our
main competitive advantages is that we operate the largest civilian cyberintelligence
network in the world. We track 4 trillion threat indicators and update these at a rate of 200,000 new
threats per second from hundreds of millions of mobile devices, endpoints, and servers across the globe.
We secure customer data, ensure immediate access to that data from an increasing number of devices
and platforms, and protect it wherever it resides.
Our leading security and information management solutions have never been more relevant than
they are today. I am very excited to share what I believe are considerable opportunities for Symantec to
capitalize on these secular trends to optimize our businesses for growth and profitability.
ACCELERATING OUR TRANSFORMATION
In fiscal 2014, the first year of our multi-year, company-wide transformation, we implemented
several initiatives designed to improve overall performance, including: dividing sales into new business
and renewal teams and increasing sales force specialization; simplifying our organizational structure; and
announcing our new channel strategy with redesigned partner programs and incentives. These initiatives
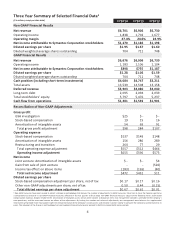
expanded non-GAAP1operating margin by nearly 280 basis points to 27.4%, in part, by reducing our sales
and marketing expenses by more than $300 million. As we completed the implementation of our go-to-
market changes, we delivered non-GAAP revenue of $6.7 billion. At the same time, we generated $1.28
billion in cash from operations and returned $918 million to shareholders in the form of dividends and
share repurchases. While we have made tremendous progress, we still have more to accomplish to
deliver on our long-term growth and margin targets.
Leading a complex transformation required us to make hard choices about our businesses and to
reexamine how we run them. To address this challenge, we organized our efforts around five key
operational priorities, which include: 1-managing our businesses as a portfolio and optimizing certain
businesses for margin; 2-prioritizing investments for growth; 3-improving efficiencies and growing
revenue through eight initiatives; 4-attracting talent to our executive team; and 5-returning significant
cash to shareholders.
1. Managing our Businesses as a Portfolio and Optimizing Certain Businesses for Margin
We’re evaluating every product line to balance profitability against growth. We’re optimizing our
more mature, lower growth Norton and storage management businesses to expand operating margin. As
part of this effort, we formed a business unit for the Norton branded products. We are simplifying our
offerings with the beta release of Norton Security and Norton Security with Backup. We are investing in
the direct-to-consumer eCommerce channel and better managing our retail and OEM channels. And, we
introduced Norton Small Business, our first Norton offering for small businesses.
We will also identify product lines to divest or end of life that don’t fit either our margin or growth
objectives.
1Non-GAAP results are reconciled to GAAP on page 4
1