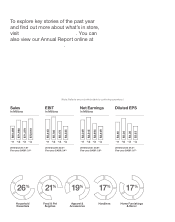
Target 2015 Annual Report Download - page 12
Download and view the complete annual report
Please find page 12 of the 2015 Target annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
A significant disruption in our computer systems and our inability to adequately maintain and update those
systems could adversely affect our operations and our ability to maintain guest confidence.
We rely extensively on our computer systems to manage and account for inventory, process guest transactions, manage
and maintain the privacy of guest data, communicate with our vendors and other third parties, service REDcard
accounts, summarize and analyze results, and on continued and unimpeded access to the Internet to use our computer
systems. Our systems are subject to damage or interruption from power outages, telecommunications failures,
computer viruses and malicious attacks, security breaches and catastrophic events. If our systems are damaged or
fail to function properly or reliably, we may incur substantial repair or replacement costs, experience data loss or theft
and impediments to our ability to manage inventories or process guest transactions, engage in additional promotional
activities to retain our guests, and encounter lost guest confidence, which could adversely affect our results of
operations.
We continually make significant technology investments that will help maintain and update our existing computer
systems. Implementing significant system changes increases the risk of computer system disruption. The potential
problems and interruptions associated with implementing technology initiatives could disrupt or reduce our operational
efficiency, and could negatively impact guest experience and guest confidence.
Data Security and Privacy Risks
If our efforts to protect the security of information about our guests, team members and vendors are
unsuccessful, we may face additional costly government enforcement actions and private litigation, and our
sales and reputation could suffer.
An important component of our business involves the receipt and storage of information about our guests, team
members, and vendors. We have programs in place to detect, contain and respond to data security incidents. However,
because the techniques used to obtain unauthorized access, disable or degrade service, or sabotage systems change
frequently and may be difficult to detect for long periods of time, we may be unable to anticipate these techniques or
implement adequate preventive measures. In addition, hardware, software, or applications we develop or procure from
third parties may contain defects in design or manufacture or other problems that could unexpectedly compromise
information security. Unauthorized parties may also attempt to gain access to our systems or facilities, or those of third
parties with whom we do business, through fraud, trickery, or other forms of deceiving our team members, contractors,
vendors, and temporary staff.
Until the data breach in the fourth quarter of 2013, all incidents we experienced were insignificant. The data breach
we experienced in 2013 was significant and went undetected for several weeks. Both we and our vendors have
experienced data security incidents subsequent to the 2013 data breach; however, to date these other incidents have
not been material to our consolidated financial statements. Based on the prominence and notoriety of the 2013 data
breach, even minor additional data security incidents could draw greater scrutiny. If we or our vendors experience
additional significant data security breaches or fail to detect and appropriately respond to significant data security
breaches, we could be exposed to additional government enforcement actions and private litigation. In addition, our
guests could lose confidence in our ability to protect their information, which could cause them to discontinue using
our REDcards or loyalty programs, or stop shopping with us altogether.
Supply Chain and Third Party Risks
Interruptions in our supply chain or fulfillment network, increased commodity, supply chain and fulfillment
costs, or changes in our relationships with our vendors could adversely affect our gross margins, expenses
and results of operations.
We are dependent on our vendors to supply merchandise to our distribution centers, stores and our guests in a timely
and efficient manner. As we continue to add fulfillment capabilities or pursue strategies with different fulfillment
requirements, our fulfillment network becomes increasingly complex and operating it becomes more challenging. If
our fulfillment network does not operate properly or if a vendor fails to deliver on its commitments, whether due to
financial difficulties or other reasons, we could experience merchandise out-of-stocks, delivery delays or increased
delivery costs that could lead to lost sales and decreased guest confidence, and adversely affect our results of
operations.
In addition, a large portion of our merchandise is sourced, directly or indirectly, from outside the United States, with
China as our single largest source. Political or financial instability, currency fluctuations, trade restrictions, the outbreak
7