Google 2015 Annual Report Download - page 15
Download and view the complete annual report
Please find page 15 of the 2015 Google annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
Table of Contents Alphabet Inc. and Google Inc.
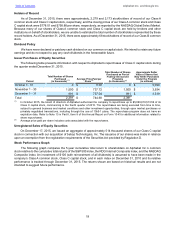
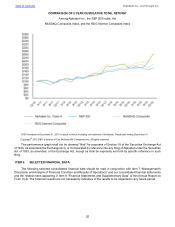
11
Any significant impairment of our intellectual property rights could harm our business and our ability to compete.
Also, protecting our intellectual property rights is costly and time consuming. Any increase in the unauthorized use of
our intellectual property could make it more expensive to do business and harm our operating results.
We may be subject to legal liability associated with providing online services or content.
We host and provide a wide variety of services and products that enable users to exchange information, advertise
products and services, conduct business, and engage in various online activities both domestically and internationally.
The law relating to the liability of providers of these online services and products for activities of their users is still
somewhat unsettled both within the U.S. and internationally. Claims have been threatened and have been brought
against us for defamation, negligence, breaches of contract, copyright or trademark infringement, unfair competition,
unlawful activity, tort, including personal injury, fraud, or other theories based on the nature and content of information
that we publish or to which we provide links or that may be posted online or generated by us or by third parties, including
our users. In addition, we are and have been and may again in the future be subject to domestic or international actions
alleging that certain content we have generated or third-party content that we have made available within our services
violates U.S. and non-U.S. law.
We also arrange for the distribution of third-party advertisements to third-party publishers and advertising networks,
and we offer third-party products, services, or content. We may be subject to claims concerning these products,
services, or content by virtue of our involvement in marketing, branding, broadcasting, or providing access to them,
even if we do not ourselves host, operate, provide, or provide access to these products, services, or content. Defense
of any such actions could be costly and involve significant time and attention of our management and other resources,
may result in monetary liabilities or penalties, and may require us to change our business in an adverse manner.
Privacy concerns relating to our technology could damage our reputation and deter current and potential
users from using our products and services.
From time to time, concerns have been expressed about whether our products, services, or processes compromise
the privacy of users and others. Concerns about our practices with regard to the collection, use, disclosure, or security
of personal information or other privacy related matters, even if unfounded, could damage our reputation and adversely
affect our operating results.
In addition, as nearly all of our products and services are web-based, the amount of data we store for our users
on our servers (including personal information) has been increasing. Any systems failure or compromise of our security
that results in the release of our users’ data could seriously limit the adoption of our products and services, as well as
harm our reputation and brand and, therefore, our business. We expect to continue to expend significant resources
to protect against security breaches. The risk that these types of events could seriously harm our business is likely to
increase as we expand the number of web-based products and services we offer, and operate in more countries.
Regulatory authorities around the world are considering a number of legislative and regulatory proposals
concerning data protection, including measures to ensure that our encryption of users’ data does not hinder law
enforcement agencies’ access to that data. In addition, the interpretation and application of consumer and data
protection laws in the U.S., Europe and elsewhere are often uncertain and in flux. It is possible that these laws may
be interpreted and applied in a manner that is inconsistent with our data practices. If so, in addition to the possibility
of fines, this could result in an order requiring that we change our data practices, which could have an adverse effect
on our business and results of operations. Complying with these various laws could cause us to incur substantial costs
or require us to change our business practices in a manner adverse to our business.
Recent legal developments in Europe have created compliance uncertainty regarding certain transfers of
information from Europe to the U.S. A preliminary agreement has been reached between the U.S. and European
governments to allow for legal certainty regarding transfers of data. However, given the preliminary nature of the
agreement, some uncertainty remains, and compliance obligations could cause us to incur costs or require us to
change our business practices in a manner adverse to our business.
If our security measures are breached, or if our services are subject to attacks that degrade or deny the
ability of users to access our products and services, our products and services may be perceived as not being
secure, users and customers may curtail or stop using our products and services, and we may incur significant
legal and financial exposure.
Our products and services involve the storage and transmission of users’ and customers’ proprietary information,
and security breaches expose us to a risk of loss of this information, litigation, and potential liability. We experience
cyber attacks of varying degrees on a regular basis. Our security measures may also be breached due to employee
error, malfeasance, system errors or vulnerabilities, or otherwise. Additionally, outside parties may attempt to
fraudulently induce employees, users, or customers to disclose sensitive information in order to gain access to our